Experience the Power of Productivity
Make your team 40% more efficient. Set up your account in just 2 minutes!

Risk of sensitive information being accessed by unauthorized personnel, leading to potential data breaches and security threats.

Difficulty in maintaining compliance with constantly changing regulations, increasing the risk of legal issues and penalties.
Time-consuming and error-prone reporting processes can hinder timely access to crucial business information, impacting overall efficiency.
Secure your business data by managing permissions to ensure that sensitive information is only available to authorized personnel, reducing the risk of unauthorized data exposure.
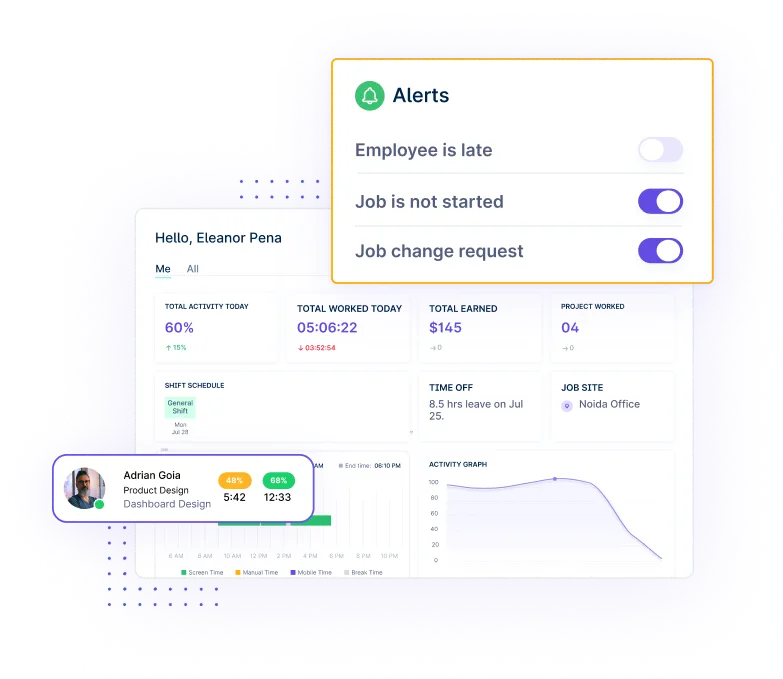
Assign access rights based on user roles to ensure that employees only have access to the data necessary for their job functions, reducing the risk of unauthorized access.

Implement detailed access controls to manage permissions at a more specific level. This will provide enhanced security and minimize the exposure of sensitive information.

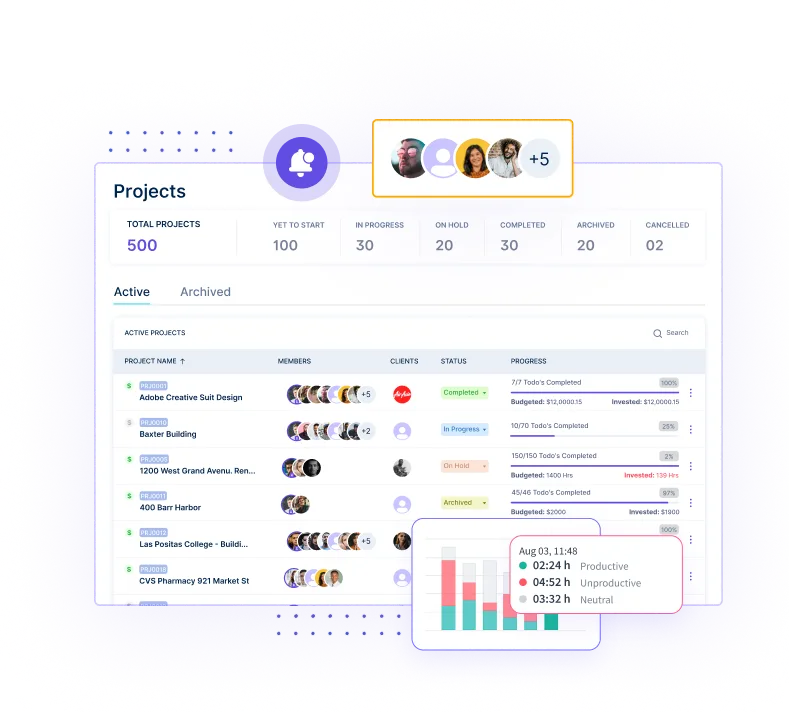
Conduct reviews and audits of access permissions to ensure they align with current roles and responsibilities and help rectify any potential security gaps.

Track use activities and identifies potential threats in real-time to prevent breaches and ensures adherence to regulatory standards.

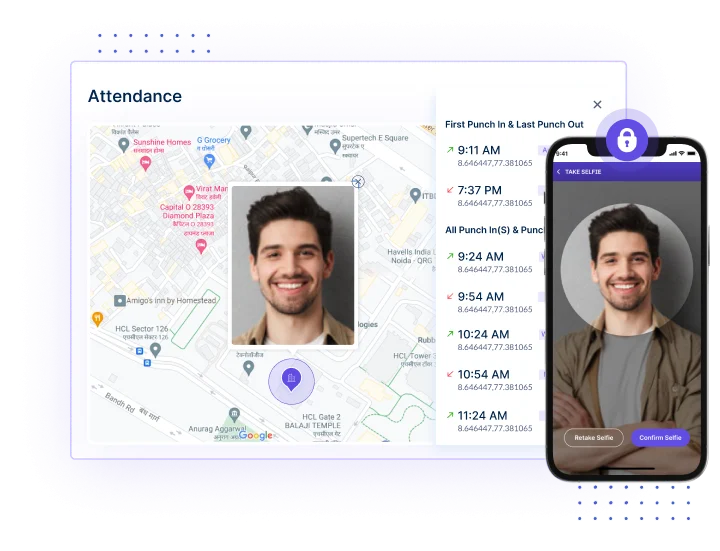
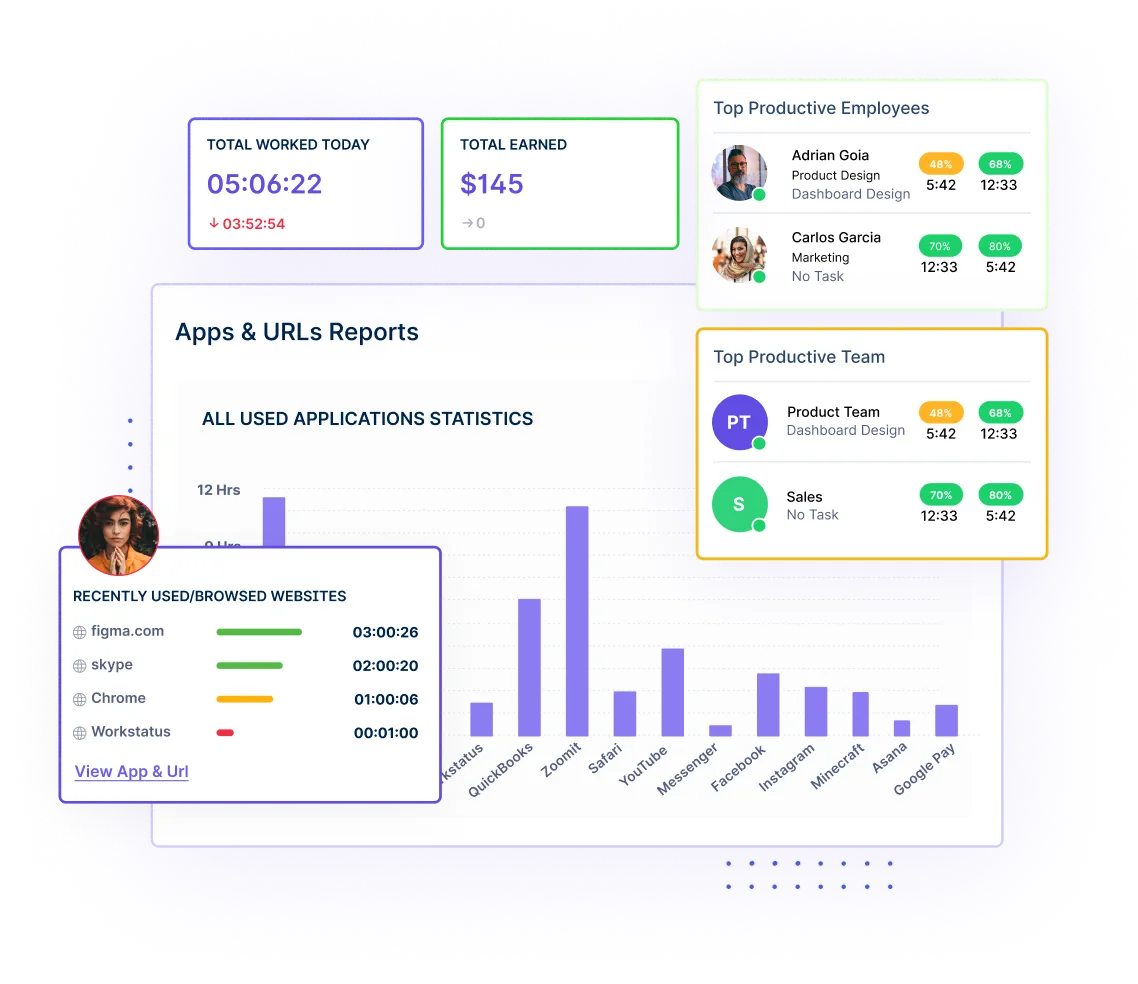
Monitor employee behavior by tracking app usage, visited websites, and capturing screenshots, ensuring compliance with company policies and identifying any suspicious activities.

Ensure adherence to regulatory standards with automated compliance checks, regularly assessing and verifying that all activities and processes meet required guidelines.

Safeguard employee data with Workstatus’s stealth mode, ensuring a silent yet robust security presence. Feel secure knowing that potential threats are monitored discreetly without disruptions.

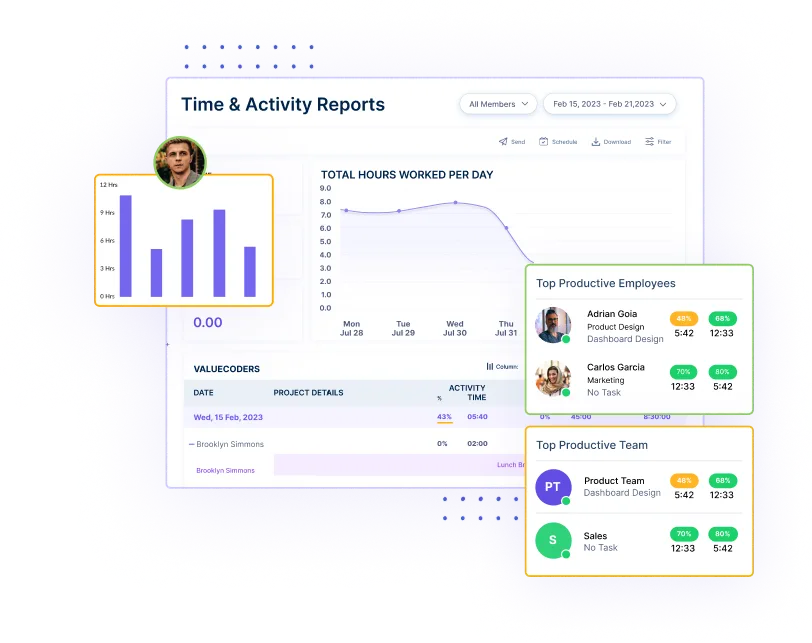
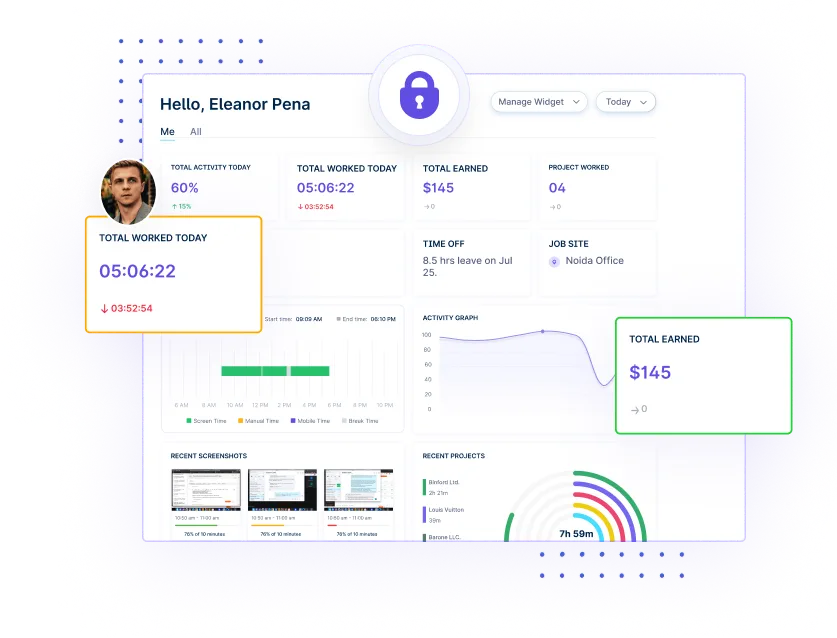
Get detailed insights into employee performance to enable timely decision-making and enhance security management.

Maintain detailed activity logs to record all user actions, providing a clear and comprehensive audit trail for security and compliance purposes.

Generate customizable reports tailored to specific needs, allowing you to focus on relevant data and gain actionable insights.

Conduct insightful trend analysis to identify patterns and anomalies, helping to predict potential issues and optimize security measures.

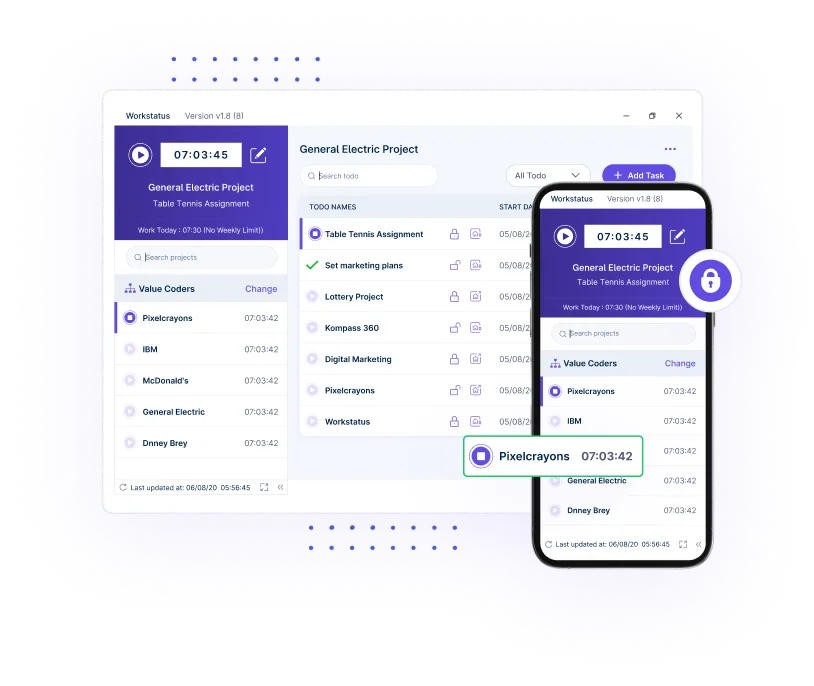
Our lightweight app allows you and your team to track time, no matter where you are. With GPS tracking and geofencing, anyone can clock in automatically when they enter a job site or get reminders based on location.
Workstatus account required to use apps
Workstatus employs robust encryption protocols and adheres to stringent security measures, ensuring that all workforce analytics data is safeguarded against unauthorized access.
Our platform prioritizes the privacy and security of your data, providing a secure environment for strategic decision-making.
Yes, Workstatus offers extensive customization options for workforce analytics. Tailor the parameters based on your organization’s unique needs, allowing you to derive insights specific to your workforce dynamics and objectives.
Time Tracking on various sites with Workstatus promotes transparency by offering a detailed account of employee presence across different locations.
This feature ensures operations are conducted accountable, providing clear insights into workforce activities and enhancing transparency.
Workstatus implements advanced security protocols for Time Tracking on various sites, preventing unauthorized access and ensuring that employees are accounted for at designated locations.
This enhances security measures, contributing to a safe and controlled work environment.
Absolutely. Workstatus’s Workforce Analytics goes beyond historical data, incorporating predictive trends to anticipate future workforce needs.
This feature empowers organizations to proactively plan for staffing requirements, enabling strategic workforce management and planning.
Track time and productivity effortlessly.
Customized Solutions for Maximum Productivity