Table of Contents
Introduction
Data theft has become a significant concern for companies of all sizes.
Safeguarding sensitive information is paramount to achieve the following:
- Protecting financial assets
- Maintaining customer trust
- Avoiding legal repercussions
This guide explores how Workstatus, a workforce management software, can help organizations prevent data theft and ensure robust data security.
Let’s dive in-
Understanding Data Theft
Data theft is a severe threat that businesses must be aware of and actively guard against. It encompasses various methods employed by malicious actors to gain unauthorized access to sensitive information.
Common types of data theft include:
- Hacking
- Phishing
- Insider threats
- Physical theft of devices or storage media
The consequences of data theft for companies can be far-reaching and detrimental.
Apart from financial losses resulting from fraud or litigation, organizations may suffer the following:
- Reputational damage
- Loss of customer trust
- Diminished competitive advantage
Compliance violations and legal repercussions can further compound the negative impact.
Organizations must prioritize data security measures and implement robust strategies to prevent data theft and its consequences.
Data Theft Stories From Around The Globe
Here are some major real-life cases that happened in the past related to data theft.
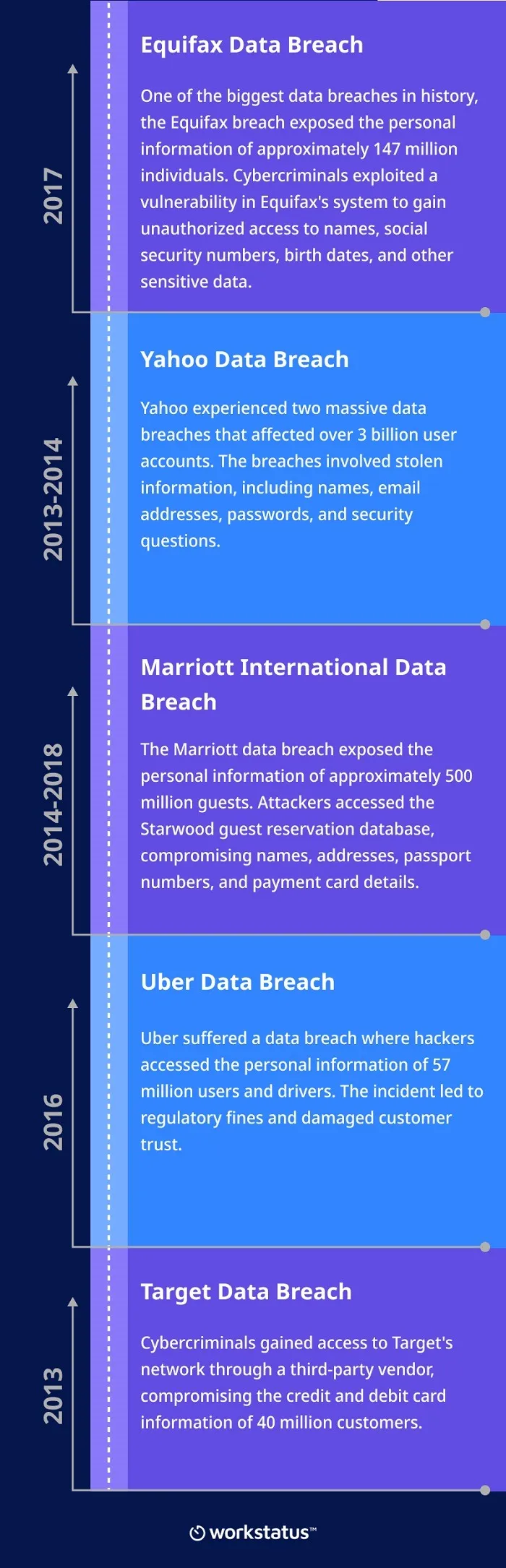
These examples demonstrate the severity and wide-ranging impact of data theft incidents.
Furthermore, emphasizes the importance of implementing a user activity monitoring system to protect sensitive information.
The Role of Workstatus in Data Security
Workstatus plays a crucial role in enhancing data security for companies.
As a powerful user activity tracking software, it offers a range of features to help you avoid the following issues:
- Cybersecurity Expenses
- Operational Disruption
- Financial Loss
- Remediation Costs
- Disruption of the Supply Chain
The Average cost of cybercrime for organizations globally increased by 11% in 2022, reaching $13 million per organization.
Overview of Workstatus as a powerful data protection tool:
- Workstatus provides secure access controls, ensuring that only authorized individuals have access to sensitive data
- It employs advanced encryption techniques to safeguard data in transit and at rest, minimizing the risk of unauthorized interception or access
Key features that help prevent data theft:
a) Real-time activity tracking: Workstatus enables companies to monitor employee activities in real-time, identifying suspicious or unauthorized behavior that may indicate data theft attempts.
b) Access control and permissions management: The software lets organizations define and enforce access control policies, ensuring employees have appropriate permissions based on their roles and responsibilities. It prevents unauthorized access to sensitive data.
c) Data encryption and secure backups: Workstatus employs strong encryption protocols to protect data from unauthorized access. Additionally, it facilitates regular backups, ensuring data integrity and availability even in a security breach or data loss incident.
Protecting Your Data With Workstatus
Here’s how you can protect your data with Workstatus:
Monitoring Employee Activities
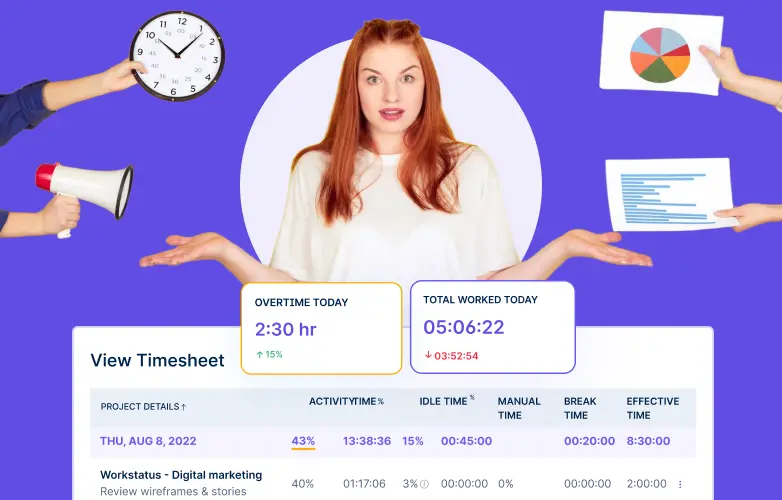
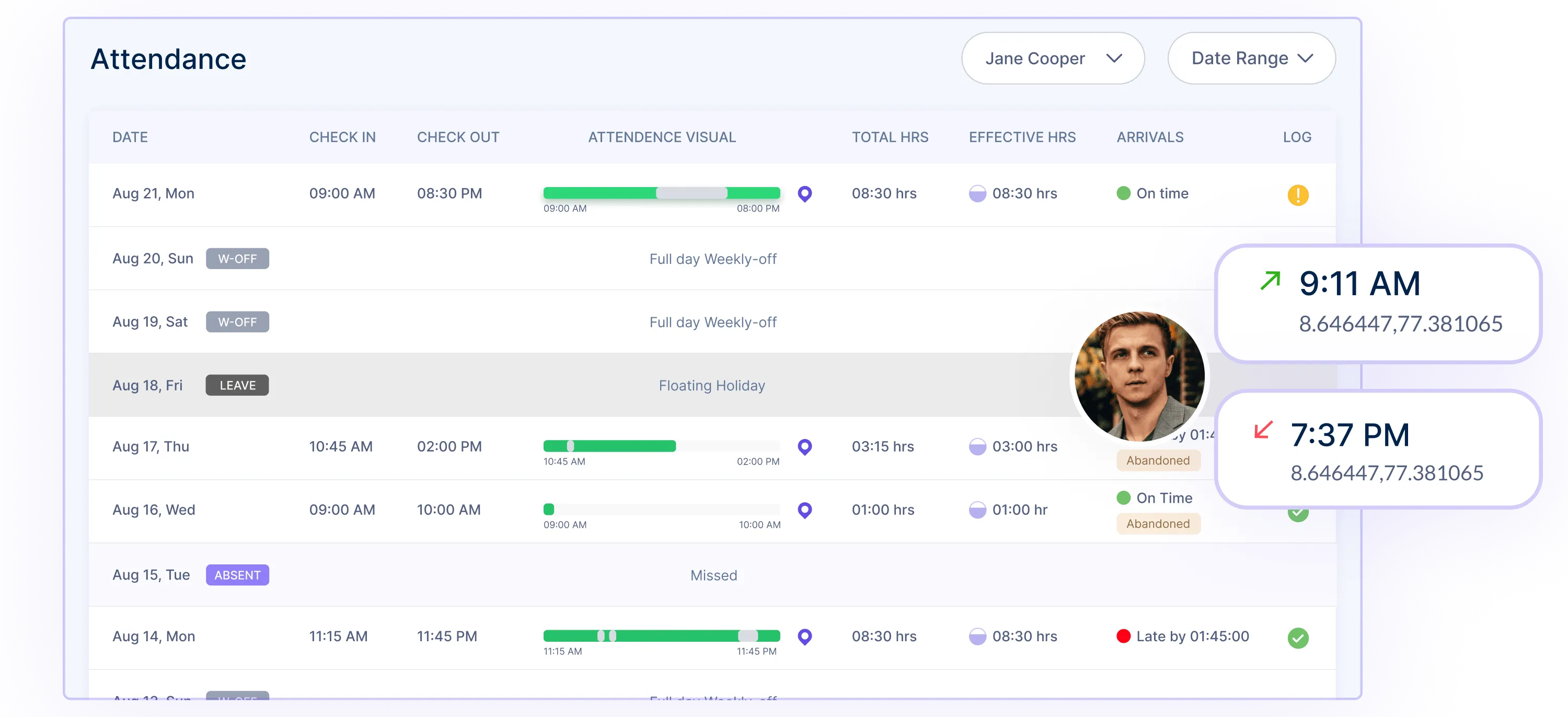
- Real-time monitoring: Track employee activities in real-time to get visibility into their work patterns, time spent on tasks, and overall productivity levels.
- Screenshots and activity logs: It captures screenshots and maintains detailed activity logs, allowing employers to review and verify the work being performed by their employees.
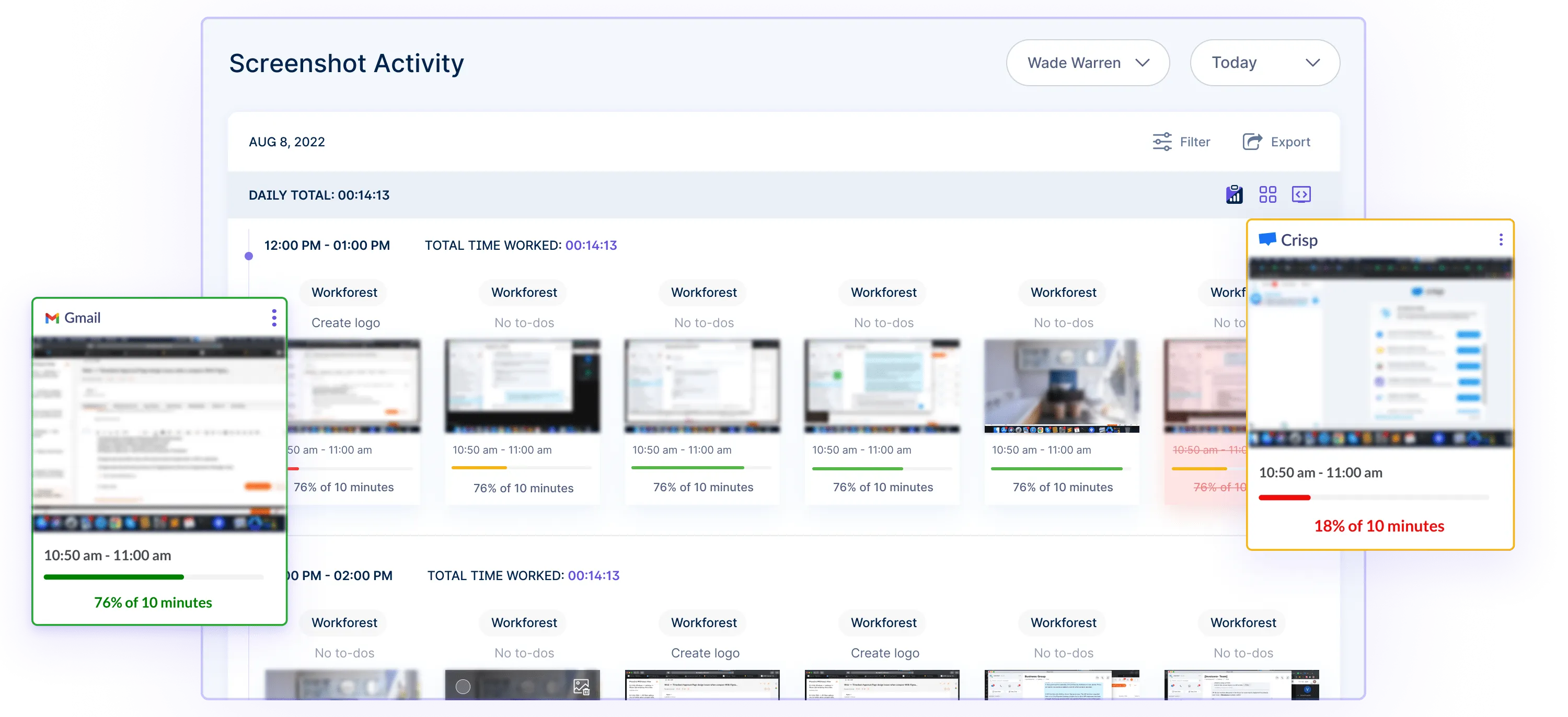
Application and website tracking: You can monitor the applications and websites accessed by employees, helping you ensure compliance with company policies and prevent unauthorized use of resources.
![]()
Identifying Suspicious Behavior
- Anomaly detection: Workstatus employs intelligent algorithms to identify patterns of suspicious behavior, such as excessive data access, unusual login locations, or irregular work hours.
- Automated alerts: It generates automated alerts and notifications when it detects potential breaches or suspicious activities like buddy punching, enabling companies to take immediate action.
- Behavior analytics: You can analyze employee behavior over time, establish baseline patterns and identify deviations that may indicate unauthorized access or data theft attempts.
Preventing Time Tampering
Selfie verification: Selfie verification ensures accurate and reliable attendance tracking, requiring employees to take a real-time selfie at clock-in and clock-out, preventing buddy punching and ensuring accountability.
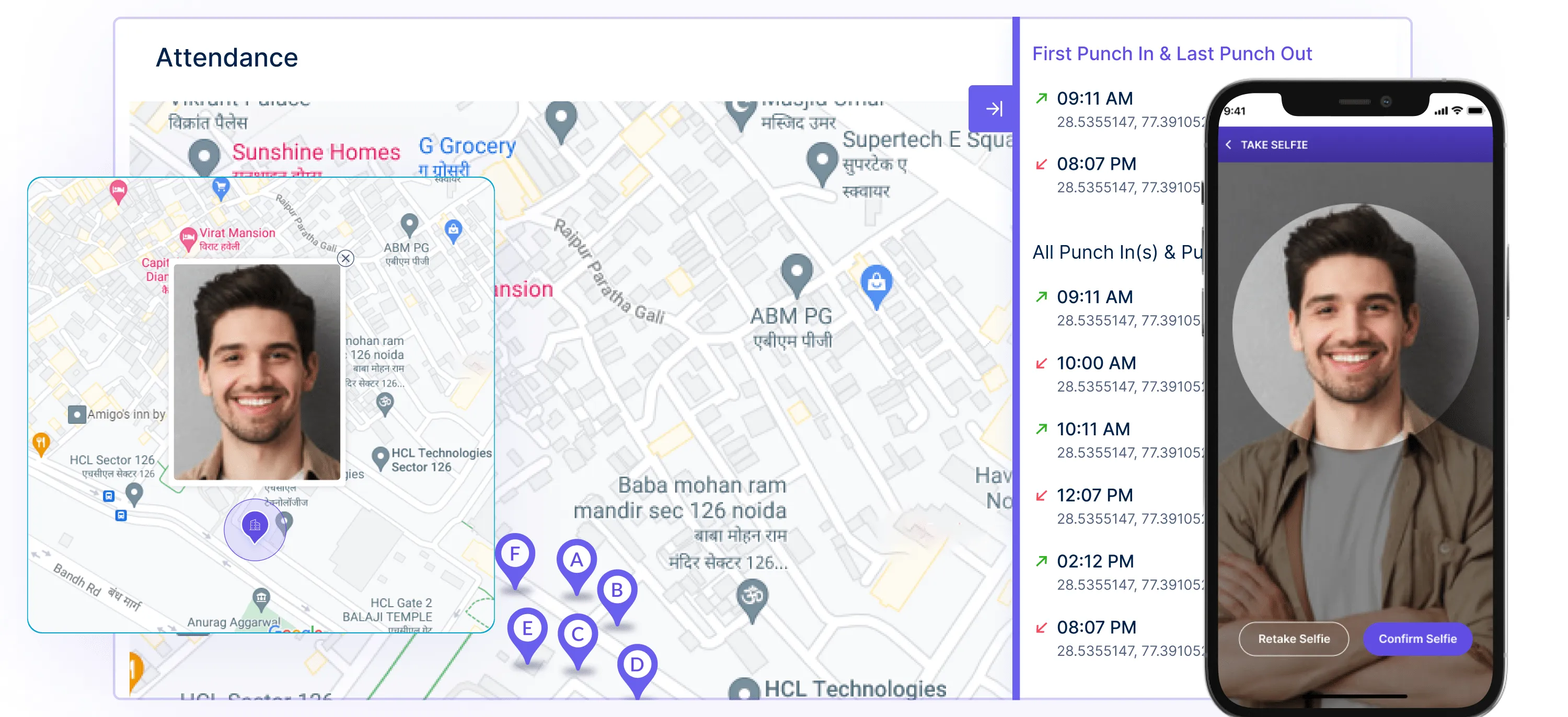
Automatic clock-in and clock-out: Workstatus eliminates manual time tracking, accurately capturing employee work hours and improving efficiency by automating the process.
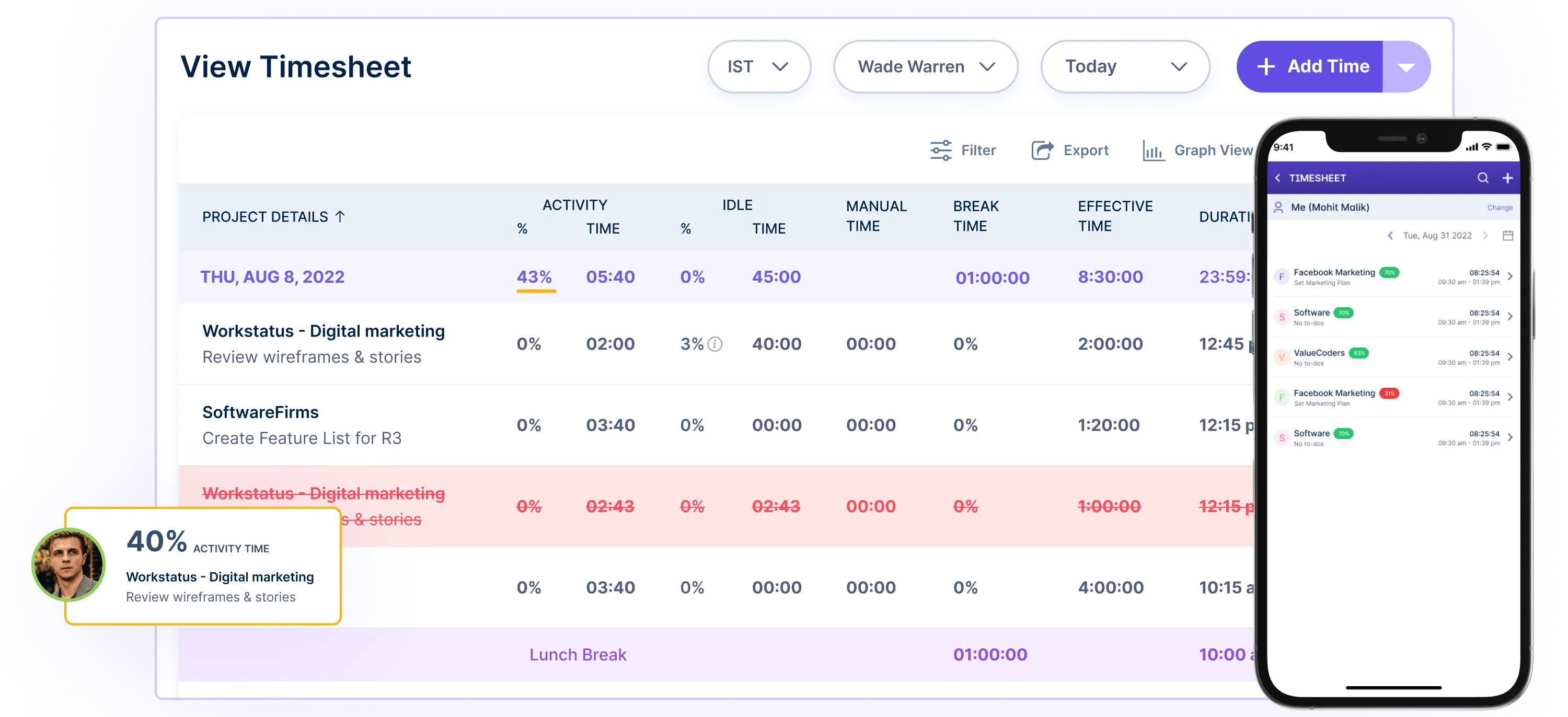
Online Timesheets: Workstatus provides online timesheets, allowing employees to log their work hours, track project time, and submit timesheets, simplifying payroll processing and enhancing accuracy in time management.
Data Reports
Adding time notes: Workstatus facilitates editing time entries by creating time notes in case anyone forgets to log their hours. It provides a centralized system for companies to manage and resolve such incidents. 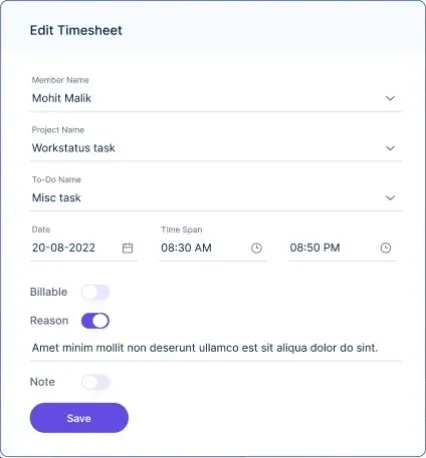
Automated reporting: Generates comprehensive reports on time, activity, attendance, timesheets, and more to help you locate any data breaches. These reports can be valuable for regulatory compliance and internal auditing purposes.
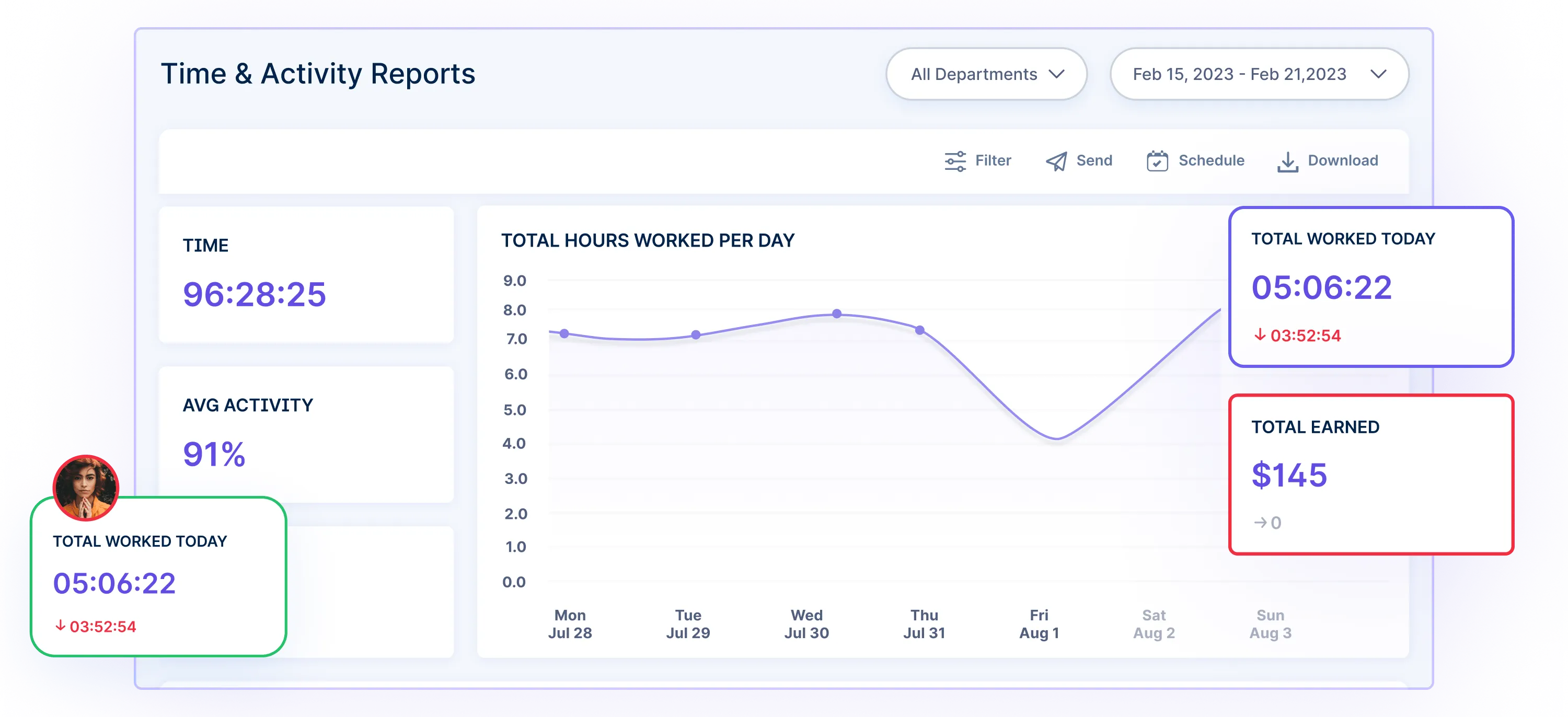
- Workflow automation: Workstatus streamlines workflows, allowing companies to define and automate processes for time tracking, attendance, scheduling, and reporting.
Compliance and Regulations
- Data protection features: Workstatus incorporates robust data protection measures, including encryption, access controls, and secure website backups, to help companies meet regulatory requirements and protect sensitive information.
- Customizable compliance settings: Workstatus offers customizable settings and policies, enabling companies to align the software with industry-specific regulations and internal compliance requirements.
Data Center Certifications of Workstatus
Workstatus demonstrates its commitment to providing secure and reliable services, ensuring the protection and privacy of client data.
Here are its data center certifications:
- ISO 9001 Quality management
- ISO 14001 Environmental management
- ISO 22301 Security and resilience
- ISO 27001 Information security management
- ISO 50001 Energy management
- SOC 2 Type II Data Security and Privacy
- PCI-DSS Information security
Workstatus showcases its dedication to maintaining the highest data center security standards and ensuring client data’s confidentiality, integrity, and availability.
The average cost of a data breach was $3.86 million, including expenses related to detection, response, notification, and lost business opportunities.
Best Practices for Data Security
It’s time to look at some of the best practices for data security.
1. Implement Strong Access Controls
Utilize robust access controls, including the following:
- Multi-factor authentication
- Strong passwords
- Role-based permissions
It is to ensure that only authorized individuals can access sensitive data.
2. Regularly Update and Patch Systems
Keep applications, software, and operating systems up to date to address any known vulnerabilities and minimize the risk of unauthorized access.
3. Conduct Employee Training and Awareness Programs
Educate employees about data security best practices, including the importance of strong passwords, recognizing phishing attempts, and handling sensitive information.
Regular training sessions and awareness programs help create a security-conscious culture within the organization.
4. Encrypt Data
Implement encryption techniques to protect data both in transit and at rest.
Encryption makes sure that even if data is intercepted or stolen, it remains unreadable and useless to unauthorized individuals.
5. Backup Data Regularly
Implement a robust data backup strategy to ensure critical information is regularly backed up.
Also, make sure that it can be restored during a data breach, system failure, or natural disaster.
Closing Thoughts
Preventing data theft is crucial for organizations to protect their financial assets, maintain customer trust, and comply with regulations.
Workstatus, with its robust data security features, including monitoring employee activities, identifying suspicious behavior, data reporting, and compliance with regulations, empowers companies to safeguard their sensitive information.
By leveraging Workstatus, you can mitigate the risk of data theft, enhance their data security posture, and ensure a secure environment for their valuable data assets.
Protect Your Data Now.
Discover How Workstatus Can Safeguard Your Business Against Data Theft.